Welcome to my first blog post about Google Cloud Platform, where we’ll take an exciting journey into the world of Google Cloud. Whether you’re new to cloud computing or just curious about Google Cloud, this post is perfect for you. We’ll be exploring some of the most frequently asked questions about Google Cloud, including what it is, how it’s organized, and most importantly, how its infrastructure is secured. Get ready to discover what makes Google Cloud unique. So, let’s get started and explore the world of Google Cloud together
An overview of Cloud Computing
Cloud computing is a technology that has revolutionized the way businesses and individuals access and store data and applications. In the simplest terms, cloud computing refers to delivering computing resources, such as servers, storage, databases, and software, over the internet as a service, rather than owning and maintaining physical hardware and software. This delivery model allows for a flexible and scalable approach to computing, enabling businesses and individuals to access the resources they need, when they need them, without the hassle of managing and maintaining hardware and software.

There are several key characteristics that define cloud computing and make it a popular choice for businesses and individuals. These include:
- On-demand self-service: Cloud computing provides users with the ability to quickly and easily provision computing resources, such as virtual machines, storage, and databases, without the need for human intervention. This allows businesses to quickly scale up or down as needed, without the need for IT support.
- Broad network access: Cloud computing resources can be accessed from anywhere in the world, as long as the user has an internet connection. This allows for greater flexibility and mobility, enabling employees to work from anywhere and access the resources they need.
- Resource pooling: Cloud computing providers typically pool resources from multiple users, allowing for greater efficiency and cost savings. Resources are dynamically allocated based on demand, ensuring that users only pay for what they use.
- Rapid elasticity: Cloud computing resources can be scaled up or down quickly and easily, allowing businesses to respond to changing demands without the need for significant investments in hardware and software.
- Measured service: Cloud computing providers typically use metering and billing systems to measure and charge for the resources used by each user. This allows for greater transparency and cost savings, as users only pay for what they use.
What is GCP ?

GCP is one of the leading cloud platforms in the market, offering a wide range of services, including infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS). With GCP, businesses and developers can access powerful computing resources on-demand, scale their applications easily, and benefit from Google’s expertise in data analytics and machine learning.
GCP has become increasingly popular in recent years, thanks to its advanced technology and competitive pricing. Many businesses are now moving their operations to the cloud, and GCP is often the platform of choice for companies looking for a reliable and innovative cloud provider.
Whether you’re a developer looking to build and deploy web applications, or a business looking to streamline your operations and improve your bottom line, GCP has the tools and resources you need to succeed in the cloud.
IaaS , PaaS and SaaS
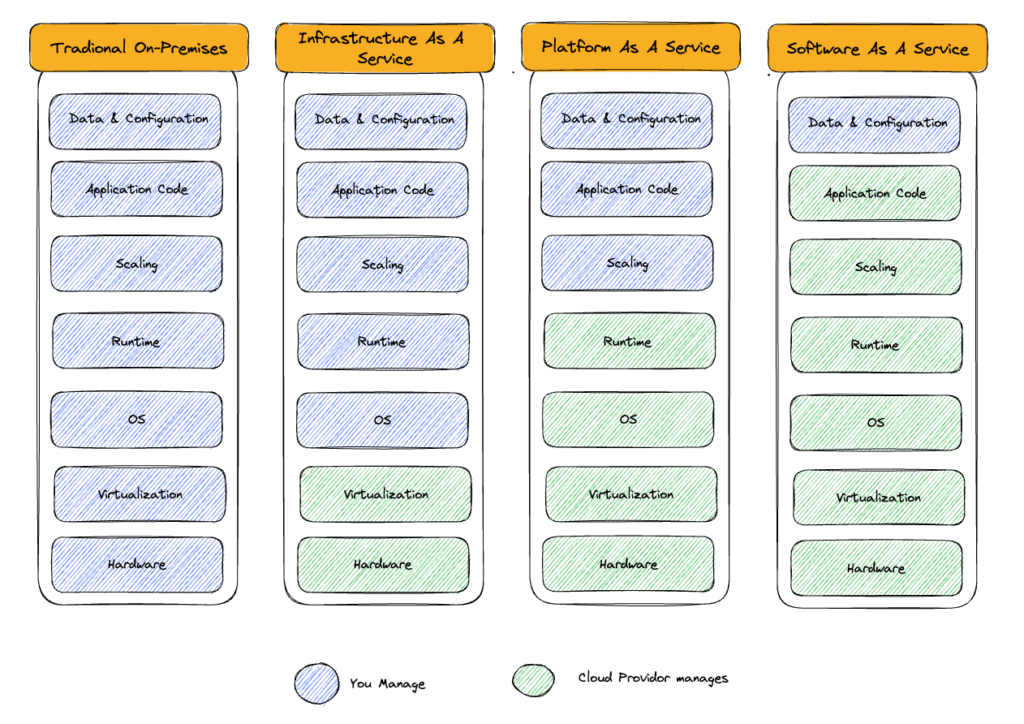
Cloud computing service models are divided into three main categories: Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). All three provide fully managed resources over the internet, such as storage, virtualization, hardware, software, and applications. The difference lies in which resources you manage and which ones are managed for you.
“As a Service” refers to cloud computing services managed by third-party providers. It’s essential to know what you want to manage when choosing a cloud service.
Depending on the service type, providers manage different elements of your computing stack:
- IaaS: Providers offer on-demand access to infrastructure services like computing, storage, networking, and virtualization. You manage the rest, including virtual machines, operating systems, middleware, apps, and data, without maintaining your own data center infrastructure.
- PaaS: Providers supply and manage all hardware and software resources required for app development. You write the code and manage the apps and data, but the platform is maintained by the provider. PaaS manages more resources to reduce the operational burden on developers and IT teams.
- SaaS: Providers deliver and manage the entire application stack through the internet. They handle updates, bug fixes, and maintenance for all components. You just need to connect to the app.
IaaS: Infrastructure as a Service
IaaS (Infrastructure as a Service) is a cloud-based service model that provides essential infrastructure components, like computing power, storage, networking, and virtualization, to businesses and individuals on an as-needed basis.
The appeal of IaaS lies in the fact that obtaining traditional computing resources to execute applications or store data can be both time-consuming and expensive. Companies must go through lengthy procurement processes to purchase hardware, allocate dedicated spaces equipped with proper power and cooling, and then hire IT experts to manage and maintain the systems.
Scaling these resources to meet increasing demand or business growth can be challenging. There’s always the risk of running out of capacity or over-investing in infrastructure that ends up being underutilized. IaaS simplifies this process by offering a flexible, cost-effective alternative to traditional IT infrastructure management.
Google Cloud Platform (GCP) offers various IaaS services. Some of the key IaaS services provided by GCP are:
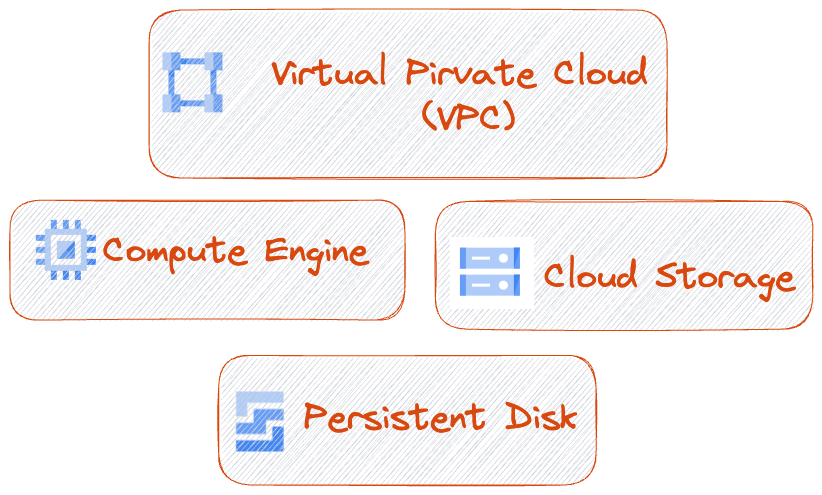
- https://cloud.google.com/compute
- https://cloud.google.com/storage
- https://cloud.google.com/vpc
- https://cloud.google.com/persistent-disk
PaaS: Platform as a Service
Platform as a Service (PaaS) is a cloud computing service model that provides a user-friendly, scalable cloud platform for creating, deploying, running, and managing applications. PaaS offers all the necessary tools for app development without the burden of maintaining hardware, updating the operating system, or managing development tools. Instead, a third-party provider delivers the entire PaaS environment through the cloud.
PaaS enables businesses to bypass the hassle and expense of setting up hardware or software for developing or hosting new custom applications. Development teams can simply pay as they go to access everything they need, including infrastructure, development tools, operating systems, and more.
This approach results in a streamlined, secure, and efficient app development process, allowing developers to concentrate on writing their application code.
Some of the key PaaS service provided by GCP is Cloud Run

Google Cloud Run is a serverless PaaS solution designed for container-based development, making it simple for developers to create and scale containerized apps. Cloud Run handles all aspects of container infrastructure, so developers don’t need to worry about starting, scaling, or managing it. Additionally, it comes with built-in security features like vulnerability scanning, dependency analysis, and tools for source provenance and attestation.
SaaS: Software as a Service
You likely use SaaS products every day! SaaS products are web-based software applications. Examples include Gmail, Google Docs, Salesforce, and Showpad (if you haven’t used them, you’re missing out!). These aren’t just ordinary websites; they’re software running in the cloud, replacing traditional email clients and office suites installed on your computer. Since they’re cloud-based, you can access them from anywhere without installation. Google groups the mentioned services under the “G Suite” name, offering them for free to personal users and at a low cost with significant benefits for businesses.

GCP Network
Google’s global network is ingeniously crafted to offer customers unparalleled throughput and minimal latencies for their applications. With over 100 strategically placed content caching nodes across the globe, this network ensures rapid access to in-demand content. By responding to user requests from the optimal location, Google’s network consistently delivers lightning-fast response times, elevating the user experience to new heights.
Infrastructure locations
Google Cloud’s infrastructure spans five key geographical regions: North America, South America, Europe, Asia, and Australia. The presence of multiple service locations plays a crucial role, as the choice of application hosting significantly impacts factors such as availability, durability, and latency—the time it takes for a data packet to journey from its origin to its destination. For instance, hosting an application closer to its user base in Europe will result in lower latency and improved performance for those users, compared to hosting it in North America.
Each of these geographical areas is further subdivided into a variety of distinct regions and zones.
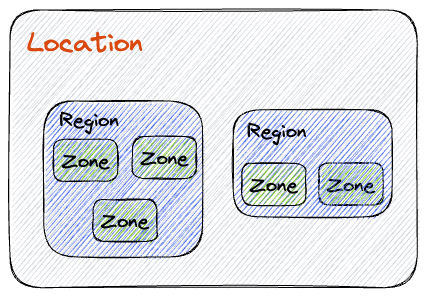
Regions
Regions represent distinct geographical areas, each encompassing multiple zones. Regions are designed to ensure data redundancy and high availability across various locations, while zones are isolated units within a region, functioning independently from one another. This structure allows for a robust infrastructure that can tolerate failures and minimize latency.
For example, consider the region of Tokyo, identified as asia-northeast1. This region is made up of three separate zones, labeled as asia-northeast1-a, asia-northeast1-b, and asia-northeast1-c. By distributing resources and applications across these zones, businesses can achieve enhanced resilience and performance for their users in the Asia-Pacific area.
Zones
Zones play a critical role in minimizing latency and enhancing fault tolerance. By strategically deploying applications and resources across multiple zones, businesses can maintain consistent performance and reduce the impact of any potential disruptions. This distributed approach allows organizations to achieve optimal availability and deliver seamless user experiences, regardless of their geographical location.
Let’s consider an example of a zone within the Google Cloud Platform. In the previously mentioned Tokyo region (asia-northeast1), there are three zones: asia-northeast1-a, asia-northeast1-b, and asia-northeast1-c. Each of these zones operates independently, with its own power supply, cooling systems, and network infrastructure.
Imagine you have an e-commerce website with a large customer base in Japan. To ensure high availability and low latency for your users, you can deploy your application across all three zones within the Tokyo region. In this scenario, if one zone experiences an outage or unexpected downtime, your application would continue to run smoothly in the other two zones. This redundancy ensures that your customers can access your website with minimal disruption, providing a seamless and satisfying user experience.
Certain Google Cloud services enable the deployment of resources in what is referred to as a multi-region setup.
For instance, Cloud Spanner’s multi-region configurations permit the replication of database data across not only multiple zones but also multiple regions, as determined by the instance configuration.
By including extra replicas, you can efficiently access data with minimal latency from various locations in close proximity to or within the regions specified in the configuration, such as The Netherlands and Belgium.
As of now, Google Cloud boasts 112 zones across 37 regions, with continual expansion underway. For the most current information, visit cloud.google.com/about/locations.
GCP infrastructure Security
security remains a top priority for Google’s workforce. Security by design is a fundamental aspect of the infrastructure upon which both Google Cloud and Google services rely.
Allow us to discuss several methods employed by Google to safeguard customer data.
Secure low-level infrastructure
In this section, we’ll provide a simplified overview of Google’s technical infrastructure security, focusing on three main areas: Security of Physical Premises, Hardware Design and Provenance, and Secure Boot Stack and Machine Identity.
- Security of Physical Premises : Google’s data centers are like high-security fortresses, equipped with advanced measures like biometric identification, metal detectors, and cameras. Even when Google hosts servers in third-party data centers, they add their own extra layers of security to ensure the utmost protection.
- Hardware Design and Provenance : Imagine Google as a master craftsman, meticulously designing server boards and networking equipment while handpicking reliable component vendors. They even create custom security chips, like the Titan, that act like elite bodyguards, verifying and protecting Google devices at the hardware level.
- Secure Boot Stack and Machine Identity : Google servers use a virtual “safety checklist” of cryptographic signatures to ensure they boot the correct software. Each server has its own unique identity, like a digital fingerprint, used for authentication and data encryption. Automated systems act like tireless sentinels, keeping software up-to-date, addressing hardware and software issues, safeguarding machine integrity, and managing access to the network. This comprehensive approach ensures a secure and reliable infrastructure for users like you.
Secure service deployment
- Encryption for Inter-Service Communication: Google’s infrastructure ensures the privacy and security of remote procedure call (RPC) data as it travels through the network. For instance, when Google Drive and Gmail services exchange information (like sharing a document via email), Google’s services interact using RPC calls. To protect your data, the infrastructure encrypts all RPC traffic between data centers by default. Google is now incorporating hardware cryptographic accelerators, allowing for the extension of default encryption to all RPC traffic within Google data centers, making these interactions even more secure.
Secure data storage
In this section, we’ll dive into how Google ensures secure data storage with a focus on two key aspects: Encryption at Rest and Deletion of Data. We’ll also provide real-world examples to make it more simple.
- Encryption at Rest Google’s infrastructure employs various storage services, such as Spanner and Colossus, as well as a central key management service. Imagine you’re storing a confidential document on Google Drive; Google’s multiple layers of encryption protect your data before it’s even written to physical storage. This encryption isolates the infrastructure from potential threats, like malicious disk firmware. Moreover, Google Cloud and Google Workspace provide key management services. For instance, Google Cloud offers Cloud KMS, allowing you to manage cryptographic keys, while Google Workspace supports client-side encryption for enhanced security.
- Deletion of Data When it’s time to delete data, Google first marks it as scheduled for deletion instead of immediately removing it. This approach allows for recovery in case of unintentional deletions. After being marked, data is deleted following service-specific policies. For example, if a user decides to delete their Google account, the infrastructure notifies relevant services handling the user’s data. These services then schedule the data associated with the deleted account for removal, empowering users to control their own data.
For more details, refer to the Data Deletion on Google Cloud documentation.
Secure internet communication
In this section, we’ll discuss how Google ensures secure communication between the internet and the services running on their infrastructure.
- Google Front End (GFE): When services want to be accessible on the internet, they register with a service called Google Front End. GFE ensures that all TLS connections are securely established using a public-private key pair and an X.509 certificate from a Certified Authority (CA). It also adheres to best practices like supporting perfect forward secrecy. Think of GFE as a security guard, monitoring and protecting the entrance to Google services.
- Denial of Service (DoS) Protection: Google’s vast infrastructure is like a fortress that can effortlessly absorb many DoS attacks. Moreover, Google has implemented multi-tier, multi-layer DoS protections to further minimize the risk of any impact on a service running behind GFE. This means that when you use Google services, you can trust that they’re well-protected against potential cyberattacks.
- User Authentication: The next layer of defense for secure communication is the central identity service, which users interact with through the Google login page. This service requests a username and password, and may also challenge users for additional information based on risk factors, such as logging in from a new device or an unfamiliar location. Once authenticated, the identity service issues credentials like cookies and OAuth tokens for future calls. To enhance security, users can employ second factors like one-time passwords (OTPs) or phishing-resistant security keys such as the Titan Security Key. This physical token supports the FIDO Universal 2nd Factor (U2F), an open standard developed by Google in collaboration with the FIDO Alliance. Many web platforms and browsers have since adopted this open authentication standard, ensuring a secure and seamless login experience for users.
Operational security
This section highlights Google’s approach to developing infrastructure software, safeguarding their employees’ devices and credentials, and defending against potential threats to the infrastructure from both internal and external sources.
- Intrusion Detection: Google utilizes rule-based and machine learning systems to alert operational security teams about potential incidents. They also conduct Red Team exercises to evaluate and enhance their detection and response mechanisms.
- Minimizing Insider Risks: Google stringently restricts and actively monitors the activities of employees with administrative access to the infrastructure.
- Employee U2F Adoption: To protect against phishing attacks targeting Google employees, the use of U2F-compatible Security Keys is required for their accounts.
- Software Development Practices: Google maintains a central source control system and mandates two-party review for new code. Developers are provided with libraries that prevent the introduction of certain types of security vulnerabilities. Furthermore, Google runs a Vulnerability Rewards Program that offers financial incentives for those who can discover and report bugs in their infrastructure or applications.
Google Cloud : Open-source friendly
In the cloud computing landscape, vendor lock-in is a common concern for many users. They worry that migrating their workloads to the cloud might make it difficult to switch providers if needed. However, Google Cloud is dedicated to ensuring that customers have the flexibility and freedom to move their applications elsewhere if they decide that Google is no longer the best fit for their requirements.
Google’s commitment to open-source technology plays a vital role in preventing vendor lock-in. By publishing key components of their technology under open-source licenses, Google fosters ecosystems that offer customers alternative options beyond Google’s own services. This open-source approach empowers users with the flexibility to migrate or switch between different providers while leveraging the same technologies.
For example, Google’s contributions to projects like Kubernetes, TensorFlow, and Apache Beam demonstrate their commitment to open-source principles. These tools can be used on various cloud platforms, giving customers the freedom to choose the best provider for their needs without the fear of being locked into a particular vendor. This commitment to openness not only benefits Google Cloud users but also contributes to the overall growth and innovation in the cloud computing industry.

Google Cloud Pricing and Billing
Google Cloud Platform (GCP) has designed its pricing and billing structure to be flexible, cost-effective, and customer-friendly, making it an attractive choice for businesses of all sizes. Here are some key features that set GCP’s pricing apart:
- Pay-as-you-go pricing: GCP follows a pay-as-you-go pricing model, ensuring that customers only pay for the resources they actually use. This approach eliminates the need for upfront investments and allows businesses to scale their infrastructure as they grow, without worrying about over-provisioning or underutilizing resources.
- Sustained use discounts: Google Cloud automatically provides sustained use discounts to customers who run their workloads on GCP for extended periods. This means that the longer you use GCP services, the more cost-effective they become, making it an ideal choice for long-term projects and consistent workloads.
- Per-second billing: Unlike some competitors that bill on an hourly basis, GCP offers per-second billing for its compute resources. This granularity in billing helps businesses save money by paying only for the exact amount of time their resources are in use.
- Custom machine types: GCP allows users to create custom virtual machine configurations tailored to their specific needs. This feature ensures that customers pay only for the resources they require, without being restricted by predefined machine types.
- Committed use contracts: For customers with predictable workloads, GCP offers committed use contracts that provide significant discounts on resources in exchange for a long-term commitment. This option allows businesses to plan their infrastructure costs more effectively and enjoy substantial savings on their cloud expenses.
- Free tier and trial credits: Google Cloud offers a generous free tier, allowing users to try out various services without incurring any charges. Additionally, new customers receive a trial credit, enabling them to explore and experiment with GCP services before committing to a paid plan.
- Transparent pricing: GCP provides clear and transparent pricing information on its website, making it easy for customers to estimate their cloud expenses. The Google Cloud Pricing Calculator is a helpful tool for generating cost estimates based on your specific requirements.
- Billing reports and alerts: To help users monitor and control their spending, GCP offers detailed billing reports and customizable budget alerts. These features enable customers to track their cloud usage and expenses, ensuring that they stay within their allocated budgets.
- Flexible payment options: Google Cloud supports various payment methods, such as credit cards, bank transfers, and invoicing, catering to the preferences of different customers and simplifying the billing process.
You may be wondering : “how can i avoid unexpectedly high Google Cloud bills ?” .
Google offers several tools to help you manage your costs :
Google Cloud allows you to define budgets at the billing account level or the project level. These budgets can be fixed limits or tied to another metric, such as a percentage of your previous month’s spend.
If your costs approach your budget limit, Google Cloud can send you an alert. For example, if you set a budget limit of $10,000 and an alert at 90%, you’ll receive a notification when your expenses reach $9,000. While alerts are usually set at 50%, 90%, and 100%, you can customize them to suit your needs.
To monitor your expenses based on project or service, Google Cloud provides a visual tool called Reports in the Google Cloud console.
Google Cloud also implements quotas to prevent over-consumption of resources due to an error or a malicious attack. These quotas protect both account owners and the Google Cloud community as a whole.
Conclusion
In conclusion, Google Cloud Platform (GCP) is a powerful and flexible cloud computing solution that provides a wide range of services and features to meet the needs of businesses and developers alike. From infrastructure as a service (IaaS) to platform as a service (PaaS) and software as a service (SaaS), GCP offers a comprehensive suite of tools that can help you build, deploy, and manage your applications and data in the cloud.
Throughout this article, we’ve explored various aspects of GCP, including its network architecture, infrastructure locations, security features, and open-source compatibility. We’ve also looked at how GCP approaches pricing and billing, and how it enables customers to monitor and control their cloud spending.
Whether you’re a small startup or a large enterprise, GCP has something to offer. By leveraging Google’s expertise in data analytics, machine learning, and other cutting-edge technologies, you can gain a competitive edge and accelerate your growth in the digital economy.
So why not give GCP a try and see what it can do for you?